Explore Users and Groups
By going in to Services > IAM, it would bring you to the dashboard. On the left panel, under Access management click on Users. From this list, you would be able to manage the users that have certain privileges in the AWS account.
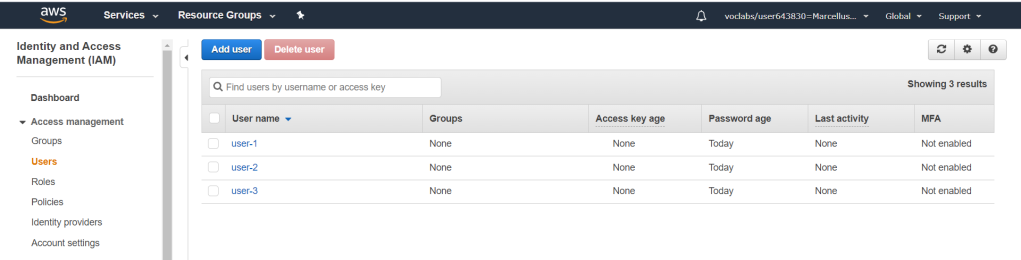
By clicking one of the users, you would be able to see or manage in more detail what kind of privileges that they have including permissions, groups and security credentials.
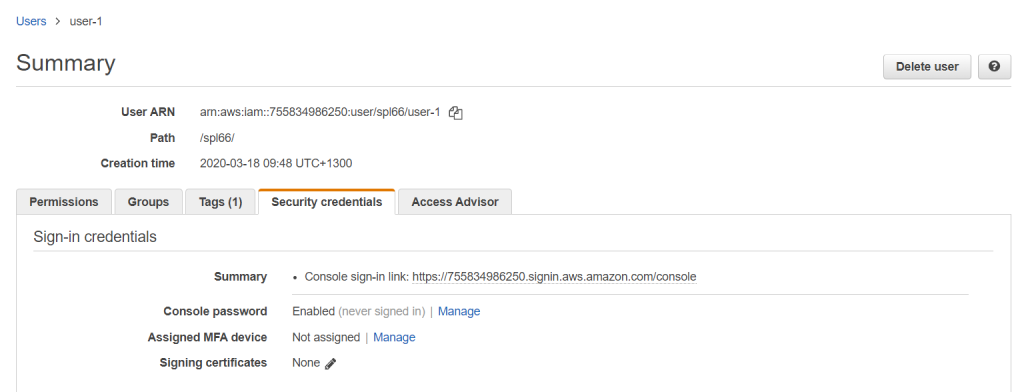
From the information provided below, we could see that this user has access to the AWS console as the console password is enabled. As an administrator, you would be able to manage all this configurations from this section and it is quite straightforward steps.
Moving on to groups. In this lab, it has been provided 3 types of group which is displayed below. It has different level of access for different services in AWS. Support are basically read only access while admin has privilege to modify certain configurations.
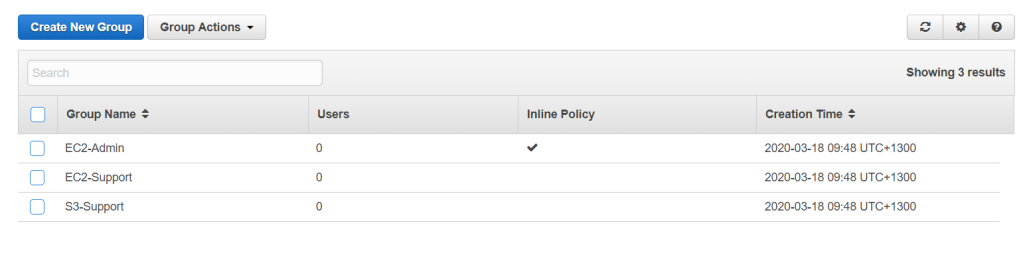
Looking at one of the groups here which is EC2-Support, it already has a certain policy attached to it. You would notice it is actually a AmazonEC2ReadOnlyAccess which is self-explanatory by itself.

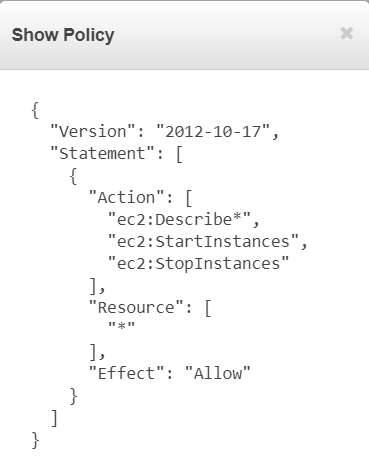
For a more in-depth detail on that policy, you could click on Show Policy to see what is in effect in the policy. As you can see, it covers ec2:Describe which lists the instances but not enabling any modification to it.
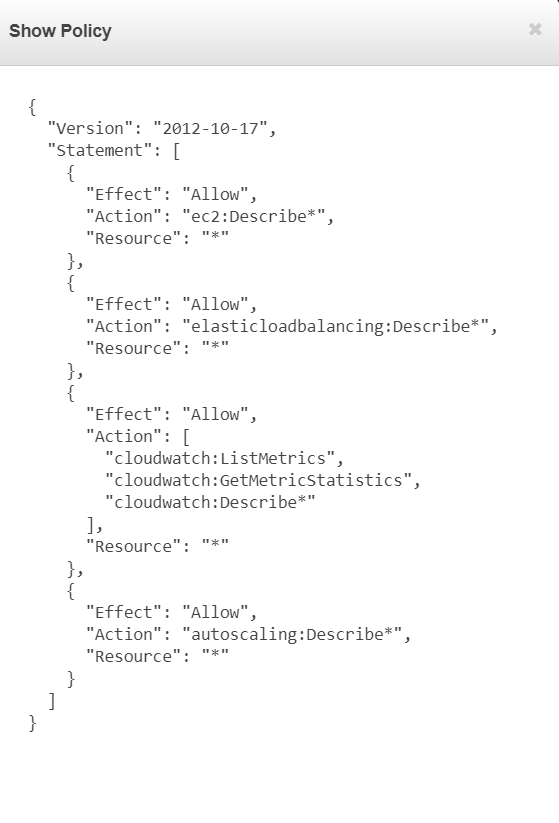
Now it will look different with the S3-Support group’s policy. You would see that it allows a Get and List for Amazon S3 service. You can conclude that this policy is actually a read-only access.
An inline policy is a bit special compared to managed policy. It provides a custom configuration for each permission. This is mostly used in a one off case where it needs special requirements.
Add Users to Groups
Initially, in this lab, we would need to assign users to the groups as provided below.
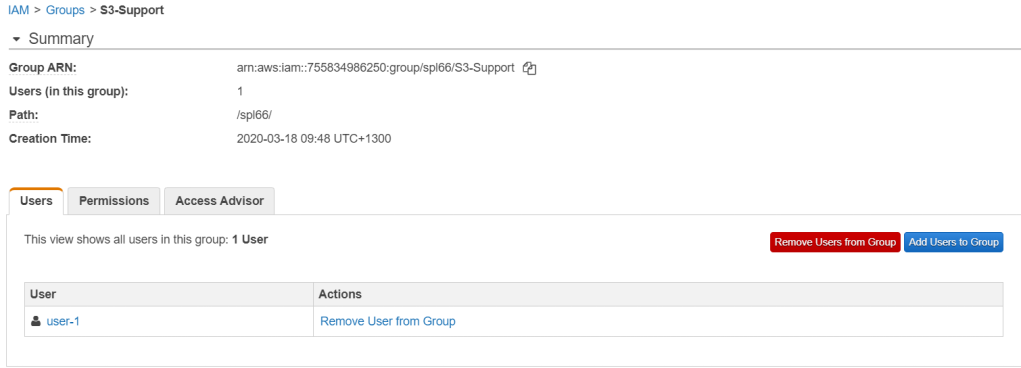
To start, we will go in to Groups and access its user tab to add the particular user. Starting with S3-Support, we will add user-1 to its users. Once assigned it will appear in the table.
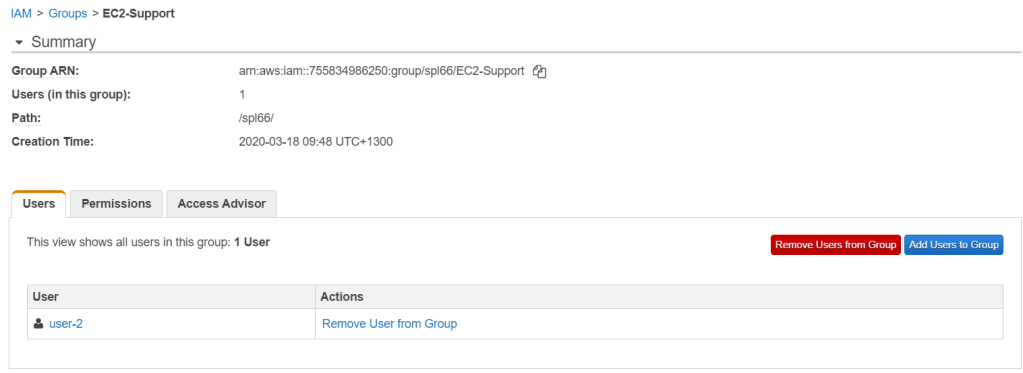
We’ll do the same thing to EC2-Support with user-2.
Assign user-3 to EC2-Admin as well.
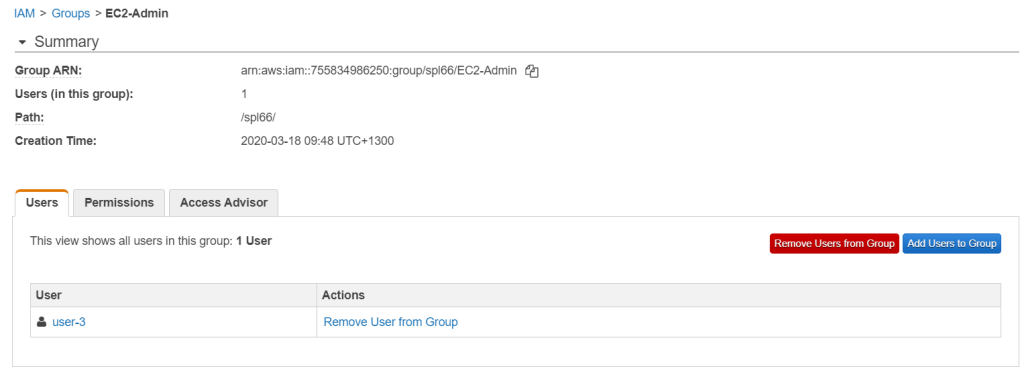
As we can see below, every group has 1 user each which we have assigned.
Sign-in and Test Users
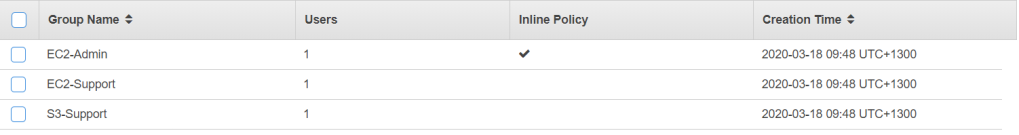
If you go to IAM dashboard, you will see an IAM users sign-in link. This link will be used for IAM users to sign in to their correct AWS server.

Opening the link in a different session will bring you to a login page where the account ID is automatically filled in. Now signing in as the user-1 will take me to the its dashboard.
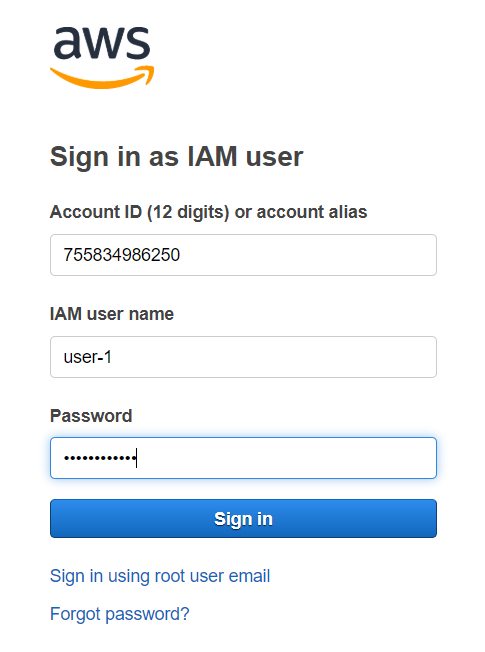
user-1 has the access to Amazon S3 bucket. Under services, access S3. In the overview tab, you will have permission to view the information inside (though there is not one in this lab environment).
With the same user, read access is not allowed for the EC2 instances.

However, as you have remembered, user-2 has read only access to the EC2 instances. So you can see below that user-2 has the permission to see the available instances. Stopping the instance, which is a modifying the instance would not be allowed from this user as it doesn’t have the permission to do so. Figure 21 shows the warning that emerge if a user tries to do so.
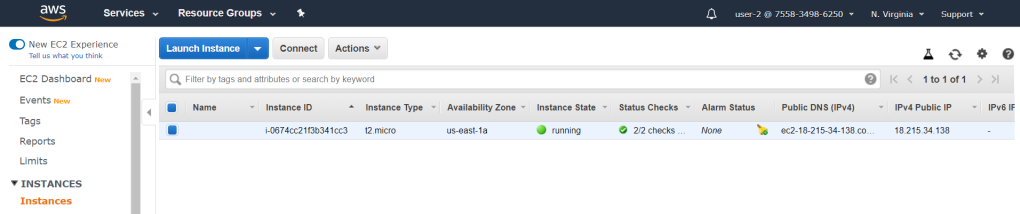

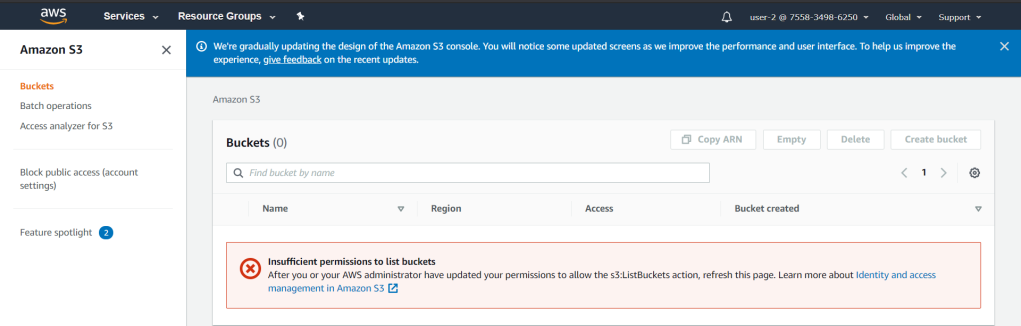
The other way around, user-2 doesn’t have the permission to read Amazon S3 buckets.
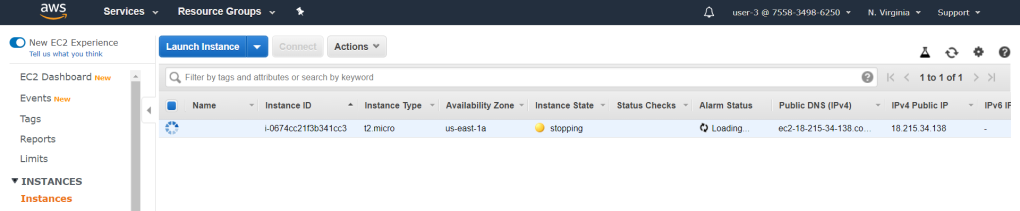
user-3 has admin access to EC2 instances. Figure 23 shows that user-3 is able to modify instances.
Users, Groups, Roles and Policies
Users relate to one individual credentials. It offers control over what one user should have and it only applies to that one individiual. The user could also have its access to the CLI as well. With users and its own credentials, they can be assigned to groups which then would be easier to manage as you would not need to manually assign each user one by one.
Groups are collections of IAM users. You can assign each group to a certain policy and it will apply to each user in the group. This make the management of policies easier as it is already grouped and could easily be changed.
Roles provide a unique approach on assigning permissions on a user. It provides temporary assignment to a certain permission. This gives the advantage to delegate access to certain services as it is configured providing permission to the assumed AWS user or services. The use of roles is for reducing potential security risk by having to many credentials spread out to AWS users or applications.
Policies are the permissions that you will assign to different identities (users, groups and roles). In writing the policy, you would provide details of explicit allow or deny for any permissions you will set in it. There are 6 types of policies in AWS IAM which are:
- Identity-based policy. This policy grants permissions to an identity.
- Resouce-based policy. This policy assign policies to resources such as Amazon S3 bucket.
- Permissions boundaries. Defines the reach of an identity-based identity to be granted access to certain resources.
- Organizations service control policies (SCPs). Specify the maximum permissions for an organizational units (OU) in the AWS Organizations.
- Access control lists (ACLs). It defines what a service could grant access to for other accounts to access.
- Session policies. This policy would grant temporary access to a certain identity for a role or federated user assignments.
Critical Thinking
Taking a few notes on the IAM features that it provides, it gives a wide range of flexibility and ease of management to the administrator. This will easily help control which identity need to be created and has what kind of permissions. Groups will make policy management easier and as well as roles.
The unique feature of roles will help in securing your cloud environment with less credentials for each application or identity which will have access to a certain resource. It also provides a temporary access to the identity assigned to the role which could give ease of access for different users to have the permission temporarily.
All this IAM management is used for security measures for the cloud environment. Thus, a well setup configruation should be applied to provide a secure environment as well as a sufficient access for each identity.
